Cyber Security Insights
Tips Attorneys Can Use to Protect Against a Cyber Attack and What to Do if You’re a Victim
APRIL 17, 2024
Your office manager accidentally clicks on a link in an email that appears to be from you. Now, a cyber criminal has gained access and is sending fraudulent emails from your office manager’s email account. These emails include instructions to clients to wire money to a cyber criminal’s account.

Source: IBM® X-Force® Threat Intelligence1
This is an example of phishing or brand spoofing, and is the most common method of data breach affecting attorneys. The act is simple: the criminal will send an email to an unsuspecting victim requesting, with some sense of urgency, that the victim click on a link or open a pdf attachment, thereby exposing the computer to malware.
Be On The Defensive
The first defenses against these scams are education and training. Your firm is as weak as its weakest link. Phishing emails will look legitimate. The days of a scammer impersonating a far-off prince who desperately needs your help are over. Now, cyber scammers are extremely sophisticated and generally part of large criminal enterprises with expertise in making the emails appear genuine. There may not be any obvious odd wording, spelling errors or other indicia of a scam. If you believe an email is “phishy,” it is best to just get on the phone (but not through the number provided in the signature line in the email). For example, if you receive an email saying that your password changed unexpectedly but you did not change it, call or contact the source from contact information not contained in the phishy email.

Source: Internet Crime Complaint Center2Do not click on email links or attachments from unknown senders, or from known senders when you were not expecting to hear from them. For example, if a prospective client emails you with an attachment or link, do not click on either until you have verified that the client is legitimate. Even if you receive an email from a trusted sender, look out for odd wording or misspellings, and verify with the sender separately – and telephonically- if you were not expecting an email.
When you receive an email with a suspicious link or attachment, investigate the email. Look at the email address of the sender and compare it to email addresses you already have from that sender. “Spoofing” is when a scammer impersonates someone you know. This is when the display name is someone you know but the email address is not. Click “details” for the email address of sender. This will enable you to see what the sender’s actual email address is rather than just the display name, which can be imitated.
Roll your mouse over the link contained in the email without clicking on it. This will enable you to see the actual web address for the link and confirm whether it was the link you were expecting. Do not “preview” the link on your phone. Do not use free public WiFi while logging in remotely (such as at a café or airport). When it is open, scammers can grab passwords and codes.
If at all possible, do an internet search for the link separately, rather than clicking on the one contained in the email. Similarly, obtain phone numbers whenever possible from an internet search rather than from email signature lines, which can include fake numbers of a spoofer rather than the legitimate number of your client or other contacts.
If you do open an attachment or click a link in an email that you think might be spam, even if seemingly nothing occurs as a result, contact your IT professional immediately. This is because the link could contain malware that can lurk in your systems even if the link did not appear to work. One way to train employees is to simulate phishing attacks, and see which employees respond.
Do not send unencrypted confidential information over unsecured electronic systems unless required. Another protection you can implement is putting an “external sender” warning on your emails. This will alert you that an email was sent from outside your firm or company. If the email looks like it came from inside the firm, such as from your paralegal, but there is the “external sender” warning message, you will know your paralegal is being impersonated.
If you utilize wire instructions, confirm the instructions telephonically on a phone number that you’ve verified separately outside of the signature line containing the instructions. If someone else is sending a wire, insist that numbers be relayed telephonically. Many attorneys now include a warning in the signature line of their emails alerting recipients that they will not send or receive emailed wire instructions. This alerts the client that any emailed wire instructions from you are likely fraudulent.
Adding Protection

Source: Internet Crime Complaint Center3Enable two-factor authentication on your computer systems, including email. This means that in addition to entering your password, your system will require an additional log in credential, such as confirmation on your cell phone, before you can access your systems. This will help prevent a cyber scammer from accessing your system remotely. Make sure your password for your computer system is complex and unique. Cyber criminals can get your password indirectly by gaining access to other accounts, then trying to use the same password to access your email account. Update your password regularly.
One of the first lines of defense is to regularly and thoroughly back up your files. Having a backup will prevent loss of data in the event of a ransomware attack. Promptly apply software and hardware updates or antivirus updates, known as “patching.” These updates can correct for new threats to your computer systems. Scammers are always at the cutting edge of vulnerabilities, and you do not want to be behind when a vulnerability is fixed. Rebooting your computer at regular intervals helps install these updates. Check the “rules” in your email account regularly. If a scammer has infiltrated your email account, they will often set up rules in your email, forwarding certain communication you receive to an email you do not recognize. If there are any rules in your account which you do not recognize, contact your IT professional immediately.
Responding to Cyberattacks
Finally, create an incident response plan to prepare for a cyberattack and stick to it. The best way to avoid liability in the event of a compromise is to have a plan in place. The plan should have an appropriate level of resiliency on how you respond to issues. The plan should also address what types of data you maintain, where it is located, and what the risk is if compromised. Make sure employees are knowledgeable about the plan.
In the event of a cyberattack, unplug your computer immediately and disconnect from the internet. If you are the infection point, unplugging your computer will keep it from “talking” to other computers on the server network. Disconnect any Wi-Fi connections immediately as well.
In the event of a breach, your firm will need a plan for communicating offline. Have an offline contact information sheet to circulate to your employees, and save it in a non-electronic place you can easily access.
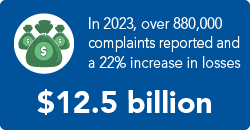
Source: Internet Crime Complaint Center4Assign an individual to be the point of contact in the event of a breach. This is the individual who will be notified first when the breach occurs and coordinate the response. If you have a cyber insurer, make sure that you also notify them immediately because they will have available resources such as forensics, ransom payment, data recovery, lost business compensation, and credit monitoring. If you are the victim of a ransomware attack, wait until direction from those on your breach plan before informing others outside of your business about the attack. Containing the information may be an integral part to getting out of the attack.
You may also have additional obligations to report the data breach to clients and authorities depending on the rules of your home state.
Following the above suggestions are a good starting point but not a guarantee that you will avoid a cyber attack. Continue to be on the lookout for suspicious emails and stay vigilant because cyber scammers keep changing the game.
* This article was prepared by Rachel Aghassi of the New York City-based law firm of Furman Kornfeld & Brennan LLP. Rachel is part of a team of lawyers and paralegals devoted to the defense of attorneys and other professionals in malpractice and disciplinary matters, as well as the defense of construction and personal-injury accidents. For more information about the above topic or the authors, please visit: www.fkblaw.com
We trust that the above article was useful and thought-provoking; however, please note that it is intended as a general guide and opinion only, not a complete analysis of the issues addressed, and readers should always seek specific legal guidance on particular matters.